Protect Your Web App with These Web Development Security Practices
When hiring a web development team, it can be hard to know what their approach is to web security. To help you better understand the principles of web security and make more informed hiring decisions, here is everything you need to know.

Content Map
More chaptersThese days, people use websites and web applications to do all sorts of things. Search for new information, collaborate with friends and co-workers, and respond to customer inquiries.
However, there are a lot of touch points, including third-party APIs (Application Programming Interfaces) and cloud-based apps. That means there are more cybersecurity vulnerabilities than ever, and failure to protect your web app from internal or external threats could spell disaster.
For these reasons, you need a web development team that takes security seriously. This article will discuss what web development security is, the different web security risks and solutions, and the best practices to follow.
Key Takeaways:
- Web development security is the practice of protecting a website or web app from cybersecurity threats.
- Common cybersecurity threats include SQL injections, cross-site request forgery (CSRF), inserting malicious code, and brute force attacks.
- When hiring a web development team, evaluate their approach to web security. Ask what steps they take to incorporate security into your product and keep it up to date.
What Is Web Development Security?
Web development security is the practice of protecting a website or web app from malicious attacks. Some of the most common web security risks include cross-site scripting, SQL injections, misconfigured security settings, and credential stuffing. These types of attacks allow threat actors to access your system and then use, disrupt, or delete your sensitive data.
Web development teams are responsible for implementing security into your web app. Their role is to implement the necessary safeguards to protect your web app from internal and external threats. Much of this is done during development and after launch through updates and security patches.

How much are companies investing in web security? In 2024, the information security market was estimated to be valued at over 200 billion U.S. dollars. This means that more and more companies are investing in web security to combat increasingly sophisticated threats.
What Are Common Web Development Security Risks?
Like all technology, advancements in web development and security are moving rapidly. Therefore, web development teams should be up to date with the latest cybersecurity risks. By doing so, this gives clients the assurance that their web apps are safe and secure.
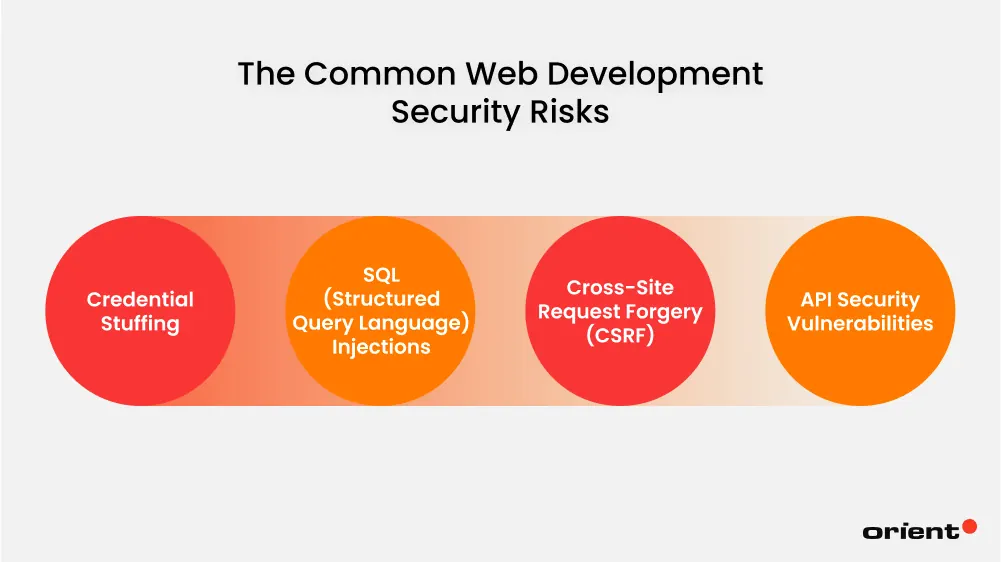
Credential Stuffing
Credential stuffing is the act of using sophisticated tools to overload a system with repeat login attempts. This is usually achieved by illegally obtaining a list of usernames and passwords from one system and then using the same user names and passwords elsewhere.
Threat actors do this in the hopes that a customer from one service uses the same username and password on another service, thereby granting them access to the customer’s accounts and sensitive data.
SQL (Structured Query Language) Injections
SQL injections exploit the way that applications submit queries to their database. It involves threat actors taking advantage of the vulnerabilities in a web app’s input fields.
By inserting malicious SQL code into a vulnerable input field, a threat actor can convince the database to trust their query. If successful, the threat actor can see, modify, and retrieve data that they otherwise should not be able to see.
In more serious cases, a threat actor may be able to grant themselves a higher access level. They can then use their stolen credentials to access even more restricted areas of the web app.
Cross-Site Request Forgery (CSRF)
CSRF is a common type of social engineering attack. The goal is to convince a user or administrator to hand over control of their accounts.
This is usually achieved by impersonating a reputable figure, such as a company boss or family member, through an email or SMS message. The message instructs the victim to perform an urgent request, such as transferring money to a new bank account or sharing sensitive credentials.
CSRF attacks are designed to come across as genuine, giving the victim little time to process the request and comply (often out of fear of retribution). How widespread are CSRF and similar attacks? 94 percent of organizations reported having email security incidents between 2023 and 2024.
API Security Vulnerabilities
APIs are third-party software that allows two or more applications to share data and functionalities. A good example of this is when an e-commerce web app uses PayPal to process its payments. The two services are unrelated, but APIs enable them to work together.
The problem is that there are many APIs, and they each vary in quality. If a business uses an API with a poor security framework, it could be at risk of an attack. A threat actor may take advantage of an API vulnerability to breach either of the two connected services. For example, if an API has no rate limiting, then a threat actor could perform a DoS (Denial-of-Service) attack to overwhelm the system.
In 2022, it was revealed that 41 percent of organizations had experienced an API security incident in the past 12 months.
What Are the Most Effective Web Development Security Strategies?
With so many cybersecurity vulnerabilities out there, it makes sense to prepare a sufficient defense plan.
When searching for a web development team, evaluate their approach to website security. This is especially important when outsourcing your web development to a third party. They should be just as vigilant about data security and compliance as you are.
Orient Software takes a proactive, structured approach to web security. Our web application development team stays up to date with emerging threats. We understand how they work, the effects they produce, and the strategies to counteract them. This enables us to incorporate the best security measures into your web app.

Here are some of the many web application security strategies we use today.
Web Application Firewalls (WAFs)
WAFs help filter out potentially malicious HTTP traffic between a web app and the internet. They help prevent threat actors from carrying out attacks like SQL injections and DoS attacks. They operate on a set of rules and policies where only approved traffic from trusted sources can access the web app.
Encryption Certificate Management
Encryption certificate management is the process of issuing, monitoring, and de-commissioning digital certificates.
A digital certificate is an executable file or electronic password that verifies the authenticity of a device, user, or server. Organizations use digital certificates to ensure that only verified users and devices can connect to their networks.
A well-configured certificate management strategy helps minimize interruptions and downtime to a minimum. It ensures a network can handle a sufficient volume of network traffic and prevents malicious traffic from breaching any connected services.
Attack Surface Management
Attack surface management is the process of using various tools to map an attack surface, identify potential cybersecurity risks, and mitigate risks.
The idea behind attack surface management is simple. It approaches cybersecurity vulnerabilities from the perspective of the threat actor, mapping out the steps they take to conduct an attack. This helps web development teams address those vulnerabilities before the service goes live.
Enforce Strict Authorization Controls
User error is a common cause of successful cybersecurity attacks. The CISO lists human error as the top cybersecurity risk. Luckily, many of these errors can be mitigated with strict authentication and access controls.
Such security controls include minimum password strength requirements, two-factor authentication, and limited login attempts. These measures force users to create unique and difficult-to-guess passwords. They also require users to provide a second form of identification to access your web app.
Best Practices to Follow for Web Development Security
Web development teams take many steps to ensure the safety and security of their products. These measures help reduce the risk of a successful data breach. They also help reduce the amount of damage that threat actors can do – even if their attacks are successful.

Document Code Changes
Documenting code changes helps web developers track the changes they make to their web apps. Such code changes may, even if unintentionally, alter the web app’s functionality. The result can lead to unintended security, performance, and compatibility issues.
For these reasons, web developers should track their code changes. This enables them to detect and address security issues – before they culminate into a major threat. The most efficient way to document code changes is to isolate any modifications from the main code repository. This way, the team can experiment without fear of damaging the web app’s functionality.
Monitor API Usage
Web apps rely on a variety of APIs to interact with third-party services. During the lifecycle of the web app, potentially unsafe and insecure APIs may become connected to its services. These are known as ‘shadow APIs’. They’re APIs that are active but no longer maintained and no longer managed by a central authority. Thus, they pose a major security risk.
Reputable web app developers use API discovery tools to identify and manage shadow APIs. These tools help ensure a safe and compliant API ecosystem. By being able to map the entire API landscape, web app developers can track every API request and response, eliminate shadow APIs, and address security anomalies.
Properly Configure Security Settings
Web apps rely on various software components to function properly. Each has its own configuration settings, which must be customized to follow best security practices. This is also known as reducing the ‘attack surface’. It involves strengthening or eliminating all of the possible entry points that threat actors may use to infiltrate your web app.
Removing unnecessary services, enforcing strict authorization controls, and updating outdated software are just some of the many ways to harden your web app’s security. Configuring firewalls to limit access and block unused access points can also help reduce the attack surface.
Build a Secure Web App with Orient Software

Protecting your web app from internal and external threats is vital to safeguarding your data and accounts. By implementing the best web app security into your product, you ensure that your web service is safe to use, protected against the latest threats, and consistently reliable.
At Orient Software, we’re passionate about helping businesses stay secure. To achieve this, we develop robust and secure web services that facilitate connections with only trustworthy services. As a result, you can be assured that your web app will maintain the integrity of your brand and be trusted by your users.
Contact us to learn more about our web development services. Find out how we can help you create an innovative web-based solution.