A project rarely goes according to plan, especially when it is as complex as a software development project. This is not to say you should be anxious at all times and constantly look over your shoulders; rather, we want to encourage a practical approach with such uncertainty during complicated processes.
This is where risk management comes in. Risk management doesn’t mean your project will be problem-free or risk-free. Rather, it provides you with reliable predictions and strategies to mitigate such risks, allowing you to move the project forward with confidence, even when facing potential risks that might derail or delay it.
Let’s dive in and learn why risk management in software engineering can bring confidence to all stakeholders, reliable frameworks and standards that can guide you, examples of common risks, and how technology can be your best friend during risk management processes.
Key Takeaways:
- Risk management in software development is the systematic practice of spotting, evaluating, and mitigating issues that may block a project from reaching its goals.
- While risk management is complicated, it keeps your company safe from the very beginning, ensures compliance, prevents costly rework, and solidifies trust from stakeholders.
- The general process of risk management involves: identification, classification, mitigation, and risk reduction planning. However, depending on the specific industry or standard (e.g., ISO 310000, COSO ERM, NIST CSF, etc.), extra steps might be involved.
- To ensure the efficiency of risk management strategies, it’s best to leverage technology to automate most of the processes.
- Risk management is not perfect. It still relies heavily on human judgment and can create a false sense of security. By keeping its limitations in mind, you can design risk management strategies that avoid blind spots and adapt to changing conditions.
Understanding Risk Management in Software Engineering
Definition
The Oxford dictionary defines risk as “the possibility of something bad happening at some time in the future; a situation that could …. have a bad result”. Risks, in the context of software development, refer to uncertainties involving security issues, budget overruns, security issues, and more.
Risk management in software development is the structured process of identifying, assessing, and addressing potential threats that could hinder a project’s success. These risks are analyzed and managed through strategies such as avoidance, mitigation, transfer, or acceptance. By making risk management an integral part of the development process, teams can reduce uncertainty, protect resources, and improve the chances of delivering high-quality software on time and within budget.
Types of Risk Management in Software Development

In order to manage risks efficiently, they are often categorized into different types. There are several ways to go about this, but in this article, we separate them based on their nature and origins.
- Technical Risks: These are risks directly involved in the development process, including security vulnerabilities, scalability issues, performance, tech stacks, etc.
- Business Risks: Business risks often involve those outside of the development phases, but impact the project, nonetheless. Misaligned requirements and changing market conditions are two examples of this type of risk.
- Operational Risks: Operational risks involve the day-to-day execution of the project, but it doesn’t involve the technical sides. For example, staff turnover or process and collaboration inefficiencies are considered to be operational risks.
Other ways of categorizing types of risks in software engineering that you might come across are:
- Internal and external risks are based on the factors that one can and can’t control.
- Inaccurate estimation risks, scope variation risks, end-user engagement risks, stakeholder expectations risks, wrong technical decisions, human resource risks, and communication risks – based on project management activities and interactions within the software development lifecycle
Reasons to Integrate Risk Management into the Software Development Life Cycle
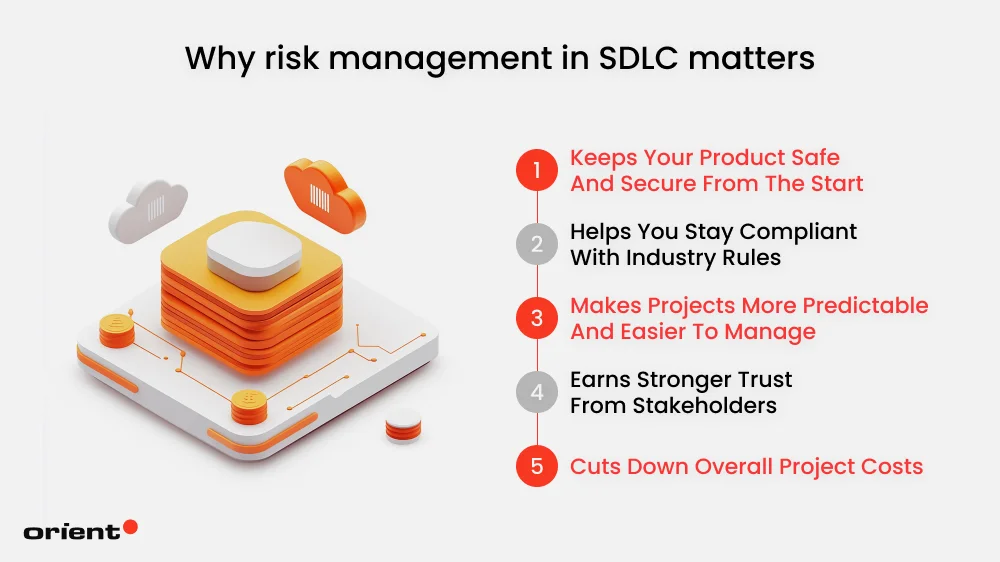
Risk management makes a workplace safer. Instead of passively waiting for each problem to come up and handling them as you move along the project, it creates a systemic approach to safeguard and minimize damage proactively. Here are reasons to integrate risk management into your development lifecycle, and a quick look at its long-term benefits.
Keeps Your Product Safe and Secure from the Start
When applying risk management strategies, teams can address and identify problems early on. The team can take preventive measures and implement safety features into the design, avoiding pitfalls and other problems. This saves valuable time from preventable problems and expensive reworks.
Helps You Stay Compliant with Industry Rules
Every industry needs to follow a number of regulations and standards. It can be challenging, however, to navigate them while going through the complex steps of building software. Failing to meet regulatory compliance can result in fines and penalties. Integrating risk management from the start ensures your compliance. With the help of the right tools and software, you can automate compliance tracking, audit trails, and reporting to make adjustments promptly.
Makes Projects More Predictable and Easier to Manage
One huge role and benefit of effective risk management is the increased confidence in decision-making. This confidence stems from having identified all potential risks and pitfalls and taken sufficient measures to prevent and mitigate them. This also leads to more effective and proactive budget planning and resource allocation.
Earns Stronger Trust from Stakeholders
A well-thought-out risk management strategy will gain confidence from relevant stakeholders. This strategy proves that the team is highly committed to the project’s success, spent time researching and addressing all potential risks, and came up with plans to proactively handle them.
Cuts Down Overall Project Costs
Identifying and detecting risks early minimizes foreseeable challenges and saves costs in the long run. The lack of proper risk management can lead to expensive mistakes and rework, and unwanted delays. The longer a risk is left unaddressed, the more time and money are needed to fix it.
Risk Management Framework and Standards
While there are several ways to carry out software risk management, there are frameworks with systematic approaches to protect businesses from financial losses and reputational damages. They act as guidelines to keep your business resilient against threats during the software development process.

ISO 31000
Developed by the International Organization for Standardization, ISO 31000 lays down a universal approach to risk management that any organization, no matter size, industry, or location, can adopt. It aims to give organizations a reliable system to make better decisions, improve efficiency, and build resilience in the face of uncertainty. In other words, it’s not just about avoiding problems; it’s about making smarter, more confident moves when risks show up.
The core guiding principles of ISO 31000 are as follows: risk management should be integrated into your processes, structured and consistent, inclusive of all stakeholders, and flexible enough to adapt as situations change. It also provides a clear framework and process, from identifying and assessing risks to treating, monitoring, and continuously improving your approach.
ISO 31000 is versatile, whether it is enterprise-level risk management or day-to-day operations. For instance, healthcare providers use it to strengthen patient safety, banks apply it to control financial exposure, and manufacturers rely on it for the supply chain.
COSO ERM
Unlike ISO 31000, which offers a universal approach, COSO ERM focuses on linking risk management directly to strategy and performance. The framework was developed by the Committee of Sponsoring Organizations of the Treadway Commission (COSO) and first released in 2004. The framework is widely adopted by publicly traded companies and even endorsed by regulators like the Federal Reserve and the FDIC.
At its heart, COSO defines enterprise risk management (ERM) as “the culture, capabilities, and practices, integrated with strategy-setting and performance, that organizations rely on to manage risk in creating, preserving, and realizing value.” In other words, this means taking a holistic view of risks involved and including them in long-term business plans. Other key benefits of COSO ERM are:
- Better alignment between risks and business objectives
- Stronger decision-making and stakeholder confidence
- A clearer connection between risk appetite, tolerance, and performance
Because of its complexity, COSO ERM is best suited for organizations with a risk committee or team of practitioners. While it doesn’t provide step-by-step guidance for measuring risks, it remains one of the most trusted frameworks for aligning risk with strategy and long-term value creation.
NIST Cybersecurity Framework
The NIST Cybersecurity Framework (CSF) is one of the most widely adopted tools for managing cybersecurity risks. NIST stands for the National Institute of Standards and Technology. The framework aims to help organizations cover the full cybersecurity lifecycle.
At its heart, the CSF revolves around three key elements: Core, Tiers, and Profiles.
- Core. The framework is built on six high-level functions: Govern, Identify, Protect, Detect, Respond, and Recover. Together, they create a continuous cycle of risk management. Each function is broken into categories and subcategories to ensure coverage across all aspects of security.
- Tiers. There are four levels to measure an organization’s cybersecurity maturity, from Tier 1 (Partial) with ad hoc processes, up to Tier 4 (Adaptive), where cybersecurity is ingrained in the culture and informed by real-time data. Moving between tiers isn’t always linear; organizations may prioritize different areas depending on industry, regulations, or risk appetite.
- Profiles. These act as a roadmap for progress. A “Current Profile” captures the organization’s existing cybersecurity posture, while a “Target Profile” defines where it wants to be. The gap between the two helps prioritize improvements and allocate resources effectively.
CSF is especially useful for IT and critical infrastructure sectors, where early detection and quick response are vital. It also aligns with standards like ISO 27001, making it a strong fit for organizations seeking robust information security practices.
You might have also come across another framework that sounds similar – NIST RMF. While NIST (CSF) provides a flexible framework for cybersecurity management, NIST (RMF) offers government agencies and contractors a systematic seven-step information security management approach.
ISO 27001: Information Security Management
ISO 27001 is the leading international standard for building an Information Security Management System (ISMS). It provides a structured framework to safeguard sensitive information through risk assessment, treatment, and continuous monitoring. The core purpose of this framework is to ensure the confidentiality, integrity, and availability of information while fostering a culture of compliance and security awareness.
The key elements of ISO 27001 include:
- ISMS Framework: Sets systematic policies and procedures that align business goals with security requirements.
- Risk Evaluation: Identifies and analyzes vulnerabilities to guide effective protection measures.
- Annex A Controls: A set of best-practice security controls covering access, cryptography, physical security, incident response, and more.
- Continuous Improvement: Regular reviews ensure defenses evolve with emerging threats.
The Processes of Risk Management
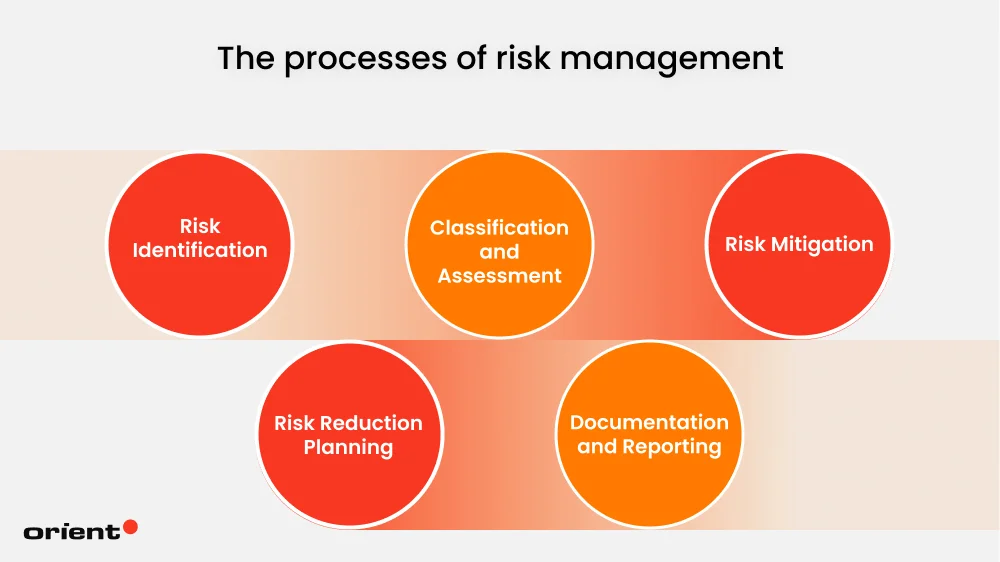
Standards and frameworks have standardized many aspects of risk management. Still, there are general steps in the process that every business needs to understand to ensure the most effective risk management strategy possible.
Risk Identification
The first step is identifying what risks the business might be facing by scanning conditions that can lead to failure in the organization. Identifying and categorizing the type of risk (operational, technical, or business) is a crucial step in preventing expensive mistakes and costly rework.
There are several methods you can use to identify and analyze risks:
- Conducting interviews with experts or business analysts gives you crucial insight into risks related to a certain focus group. Moreover, this is how you spot hidden risks involving human behaviors, like their work habits.
- Conduct a brainstorming session with team members, asking them to list potential risks, elaborate on each item, and provide feedback. This is a great way to uncover risks that might be clear to one member but not be as apparent to others.
- What better way to identify a product’s risks than by examining the product itself? Creating a working prototype allows the team to have a practical view of its vulnerabilities and the resources and budgets it might still need.
Classification and Assessment
The next step is understanding the risk by analyzing, classifying, and assessing it. There are often guidelines for each industry involving severity or probability. For example, the company can use quantitative analysis, using data to determine the financial impact the risk will have. Risks can also be classified based on their severity, for instance, to determine immediate or near-future actions.
Understanding a risk’s potential impact and consequences allows the team to come up with reasonable strategies to manage and mitigate it, while still ensuring the product is fit for the market.
Risk Mitigation
There are three main approaches in risk mitigation: preventing risks from happening, reducing their likelihood, or limiting their impact.
Based on these approaches, teams can develop suitable strategies to manage risks effectively. These strategies can be technical (e.g., automated testing, code reviews), procedural (e.g., change management workflows), or even physical (e.g., server room access restrictions). A good mitigation strategy addresses both prevention and backup plans.
Risk Reduction Planning
After nailing down the mitigation approaches and strategies, they need to be turned into an actionable plan. A risk reduction plan entails a clear timeline and assigns responsibilities and resources for each strategy or approach. This step’s goal is to ensure the mitigation strategies don’t simply stay on paper but are turned into actions.
Documentation and Reporting
Strong risk management practices are well-tracked and provide visibility for all parties involved. This means a lot of documentation that captures the entire process, so teams and stakeholders can track what’s being done. Reports or dashboards also create accountability and provide evidence for audits, regulatory reviews, or client assurances.
Common Risks in Software Development (and How to Mitigate Them)
In this section, we’ll dive into three common risks teams encounter during the development process: technical risks, third-party integration risks, and risks relating to requirement changes and scope creep.

Technical Risks
Technical risks are inevitable during the software development process. They might stem from the wrong technology stack, poor architectural design, or outdated tools. If not addressed properly, these issues can snowball into scalability challenges or security gaps.
For example, skipping or underestimating the testing phase can leave serious bugs and undiscovered vulnerabilities in the later stages of development. Add outdated tools or inexperienced developers into the mix, and your team may face undiscovered vulnerabilities, privacy concerns, and costly rework.
Solution: A strong technical leader, be it a senior developer, product manager with technical expertise, or CTO, should oversee these risks. However, when in-house knowledge falls short, consulting external experts can provide the missing perspective. With guidance from experienced architects, QA engineers, and analysts, teams can make smarter choices around technology, design, and testing, setting the project up for long-term stability and success.
Third-party Integration Risks
Third-party integrations have become almost unavoidable in modern software. From Google or Facebook sign-ups to payment gateways and CRM add-ons, they streamline workflows and save development time. But they also introduce their own set of risks:
- Outdated or inconsistent documentation can slow down development and lead to unexpected integration challenges.
- Security risks arise when sensitive data is shared with external providers you can’t fully control.
- Performance issues may emerge. For example, a payment gateway introduces latency that affects the user experience.
Solution: Treat each integration as unique. Perform careful research during discovery, validate APIs with small Proofs of Concept (PoCs), and be ready to engage directly with provider support teams. This minimizes uncertainty, avoids last-minute surprises, and ensures your product runs smoothly without being held back by someone else’s system.
Requirement Changes and Scope Creep
Requirements are the backbone of any software project. They shape design, development, testing, and long-term maintenance. Getting them wrong can be costly. The Project Management Institute found that 35% of projects fail due to poor requirements gathering.
Research and real-world experience show seven common risks tied to unclear or mishandled requirements:
- Overloaded requirements. Clients sometimes pack multiple requests into one requirement, thinking it saves time and cost, but it often creates confusion instead.
- Inappropriate representation. Pseudo-code, vague references, or unclear phrasing make requirements hard to follow.
- High interdependency. Requirements tied too tightly to others can cause a ripple effect when changes occur.
- Notes and assumptions. Relying on “understood” details often leads to building the wrong functionality.
- Unfeasible or untestable requirements. If a requirement can’t be implemented or tested, it’s a recipe for delays.
- Poor adaptability. Evolving requirements without a solid process lead to conflicting priorities.
- Vision drift. Straying from the original product vision late in development disrupts sprint planning and delivery.
Solution: Use a Software Requirements Specification (SRS). This structured document:
- Keeps requirements clear, traceable, and testable.
- Provides a single source of truth for stakeholders and developers.
- Makes adapting to changes smoother and less disruptive.
Leveraging Technology in Risk Management
Risk management is complex and requires extensive documentation and tracking. Attempting to do everything manually is an impossible feat. Leveraging technology in risk management keeps your workplace safe, minimizes mistakes, and keeps your data up to date to prevent risks.
Notable digital transformations in risk management include:
- Artificial Intelligence. AI automatically collects data in real-time, provides constant risk watching, and puts new code to use much faster.
- Predictive risk analytics. Used in tandem with other tech like AI and ML, predictive data analytics help companies spot issues even before they emerge and facilitate fast, confident decisions.
- Digital Twins. Digital twins make digital copies of their real-life subject. It allows teams to simulate tests and monitor the outcome without real-life consequences.
- Collaborative risk management platforms. Risk management should be a collective effort, where every team is looped in on the newest risks and strategies. A collaborative platform is how you keep everyone updated, on the same page, and have a single, cohesive plan for dealing with risks.
Risk Management Limitations
Risk management is powerful and offers various long-term benefits. Still, like any other tool and strategy, it comes with certain limitations and challenges.
- Complex and time-consuming. Risk management is essential; however, as it involves multiple processes and standards, it can quickly become a complicated and time-consuming feat that not every company has the right expertise and resources to execute.
- Costly. In most cases, risk management requires a trained professional to conduct an effective assessment. Risk management models, their standards and regulations are complex and hard to navigate. The recruitment and training process is expensive, and that is not to mention the tools that come with risk management.
- False sense of security. More often than not, once risk management plans are put in place, people let down their guard. In other words, teams might become complacent and not be as vigilant or take security measures as seriously.
- Heavy reliance on human judgment. No matter the tools or tech one uses to come up with risk management strategies, the key decision still relies heavily on human judgment. It goes without saying that blind spots, subjectivity or incomplete knowledge can lead to underestimating, overestimating or overlooking risks completely.
By acknowledging its limitations, you can turn risk management into a more resilient, adaptable, and future-proof strategy.
Last Note

Risk management can be complex and overwhelming, but it is essential if you are committed to the project’s success. By staying proactive and addressing risks early, you avoid costly delays, wasted resources, and compliance penalties.
Not sure where to start? That’s where Orient Software comes in. With 20 years of experience in the field, we are confident that we can help you navigate through the complexities of regulations, standards, and modern technologies. Don’t hesitate and reach out to us today!